February 6th, 2026
Improved

Using the brand new Luna Page and the new ‘Generate automation flow’ playbook, you can describe your desired workflow in natural language and have Luna automatically generate the flow for you.

Disclaimer: This feature is very much in beta and Luna will most likely make mistakes. Verify every workflow Luna generates.
February 1st, 2026
New
We’re excited to announce that we’ve released the first version of the Ploy api, allowing you to programmatically interact with Ploy. This is great for pulling data from Ploy automatically, or managing configurations via IaC tools like Terraform.
This is currently in beta so if you’d like access don’t hesitate to reach out to the team.
January 28th, 2026

Luna can now automatically generate access catalogs for you. Whether you're going through initial setup or managing catalogs day-to-day, Luna can create the catalog structure you need in seconds rather than hours. Catalogs allow you to define targeted sets of resources that employees can request access to.
How it works
You have two options:
Let Luna take the wheel - Luna will analyse your historical access patterns and generate a complete suite of catalogs tailored to your organisation

Request specific catalogs - Tell Luna exactly what you need and it will create catalogs to match

Everything Luna creates starts in draft, so you have full control to review and refine before publishing.
Regeneration with context
Not quite right? You can regenerate your catalogs with additional context to guide Luna toward better results. This is particularly powerful for fine-tuning the output to match your specific needs. Note that regenerating will replace any AI-generated catalogs currently in draft.
Fresh new look
We've also refreshed the catalog list with a more vibrant design to make managing your catalogs a better experience.

This is an early release - we'll be tuning Luna's catalog generation based on your feedback, so please experiment and let us know how it goes.
January 27th, 2026
Improved

We’ve added 3 new offboarding actions for Microsoft based identities in Ploy, Revoking sessions/sign-ins, Removing MFA devices and removing entra connected mobile devices.
This is a great way to further secure you’re identities post offboarding. To get started with these create a flow using any of these actions

January 26th, 2026
Improved

For Slack Business+ and Enterprise Grid customers, Ploy can now automatically provision and deprovision users. When someone joins your company or changes role, their Slack access follows automatically. When they leave, it gets revoked. No more chasing IT tickets or finding out three months later that a former employee still has access to your channels.
Enterprise Grid customers can also create single and multi-channel guests directly from Ploy, which is handy for managing contractors, vendors, or anyone else who needs limited access without a full account.
Improved usage data
We now pull in Slack session history alongside the existing metadata. This means you can:
See when someone last actually used Slack, not just when their account was created
Spot dormant accounts that might be worth reclaiming (or investigating)
Flag dangling access during reviews. If someone hasn't logged in for 90 days, that's probably worth a conversation
This is especially useful for access reviews where you're trying to work out whether someone still needs access or if they've quietly moved on to a different team.
January 23rd, 2026
New
The team at Ploy have hit the ground running in 2026 releasing a huge amount of features, updates and (long awaited) bug fixes to make managing access and identities in 2026 a breeze.
Let’s dive in 👇
New resources page
The biggest change is our brand new resources page which puts everything right at your fingertips. On one page you now have a much more clear breakdown of each resource including any issues Luna’s found, active, removed and shadow access as well as any access requests and usage data we have.
There’s also a heap of new actions you can take from re-granting access for removed users to quickly viewing and remediating users stuck in in-between states. Read more about it here.

Sources of truth
It’s now easier than ever to see the exact same list of users you see in an app or resource, reflected in Ploy. With sources of truth you define where Ploy gets it’s authoritative list of access for any given resource. This might be an integration, another resource (e.g. if it’s SAML/SCIM controlled) or the Browser extension.

You can also automatically associate entitlements (more on this below) with each source of truth making it easier to know and manage not only who has access to a resource but also what they can do in that resource.
👉 Get started here with sources of truth here
Entitlements
Entitlements in Ploy are now first class citizens, allowing you to easily review, manage and provision permissions, roles and other forms of access across any application and resource. We’ll automatically pull these in from integrations or via connected resources from sources of truth.

👉 Get started here with entitlements here
Custom Reports
A long overdue feature is the ability to create custom reports in Ploy allowing you to track (and manage) what’s important for you and your team. We have some prebuilt ones out of the box to help you get started but if none of these fit your needs, you can always create your own.

App auto provisioning
Previously with applications, you’d need to use a manual flow to auto provision access, or provision access through a connected resource (e.g. a SCIM group). Now you’re able to directly provision access straight from the application by selecting a resource to grant access to when access is requested.

Integrations view
We’ve also completely redesigned our integrations views making it easier to integration with new sources as well as manage existing integrations.
We’ve also added the ability for you to trigger scans manually when you need to see data live after a change in a source system.

New Integration features
New integration
We’ve just released a new HRIS integration - Personio. This will allow customers using Personio as their employee source of truth pull in all those details into Ploy.
View docs for getting setup here.
Expanded features
Github: You can now automatically grant and revoke users access to teams inside your Org. Great for JIT access to certain Github resources.
JIRA/Atlassian: Via our Flows feature, you’re now able to automatically invite users to your Atlassian organisation when they don’t yet have an account. Great for onboarding or access requests.
Microsoft: You’re now able to invite guest users to your Microsoft tenant and grant them access to any resource in Ploy and wrap access policies around their access. Great for preventing guest access lingering.
And a whole heap of other things
New
New: Bulk add tags to resources
New: Archive old integrations
New: 'Nudge Reviewers' button on admin access request view
New: Option to include/exclude shadow accounts from offboarding
New: Filter access by low usage (e.g. unused in the last 30/60/90 days)
Improved
Improvement: It’s now more clear what access reviews are ready for approval and more obvious how to approve them
Improvement: When creating offboardings manually, the end date of the employee will automatically pull in when present
Improvement: Select fields with large lists will now show a preview instead of having to search to see results
Improvement: App filters on will now persist across refresh
Bugs
Bug: Fixed issue where requesting access on behalf of users in a department would fail
Bug: Fixed bug where month placeholder on campaigns would put the month number instead of text
Bug: Can now chain multiple ‘wait for response’ survey responses and use all results in subsequent nodes
Bug: Fixed issue where unsuspending access would failing
Bug: Fixed new app column views not showing on save
Bug: Fixed annual cost edit not working in managed apps
Bug: Fixed editing campaign reviewer not applying
Bug: Fixed incorrect link for access review started notification
Bug: Fixed reminder saying review is overdue when it isn't
Bug: Fixed create new app reporting failure but succeeding
Bug: Fixed issue with merging employees
December 16th, 2025
New

We've added a new safety feature to protect against any automated process making un-intended large-scale access changes e.g. from a misconfigured rule or a policy applied to the wrong resource.

How it works:
You set a threshold (for example, 10 or 15 users). If any automated process like the low usage checker or automatic access expiry would revoke access for more users than your threshold, Ploy will pause the action and send it to an approvals screen. An admin then needs to review and approve it before it goes through. By default this threshold is set to 15 and can be configured here.

Rollback:
If something slips through, you can undo bulk revocations and restore access. Think of it like ctrl+z for access management.
November 28th, 2025

You’re now able to wrap your Just-in-time access policies around Tailscale roles, giving users elevated break glass permissions to perform sensitive actions in a secure way. Setup the Tailscale integration to get started today.
November 24th, 2025

Employees requesting access via the catalog are now able to Nudge reviewers as a reminder to review their access request, enabling employees to be in control of their requests and reducing IT workload. In coming updates, Luna will automatically keep on top of access requests

November 24th, 2025
Improved
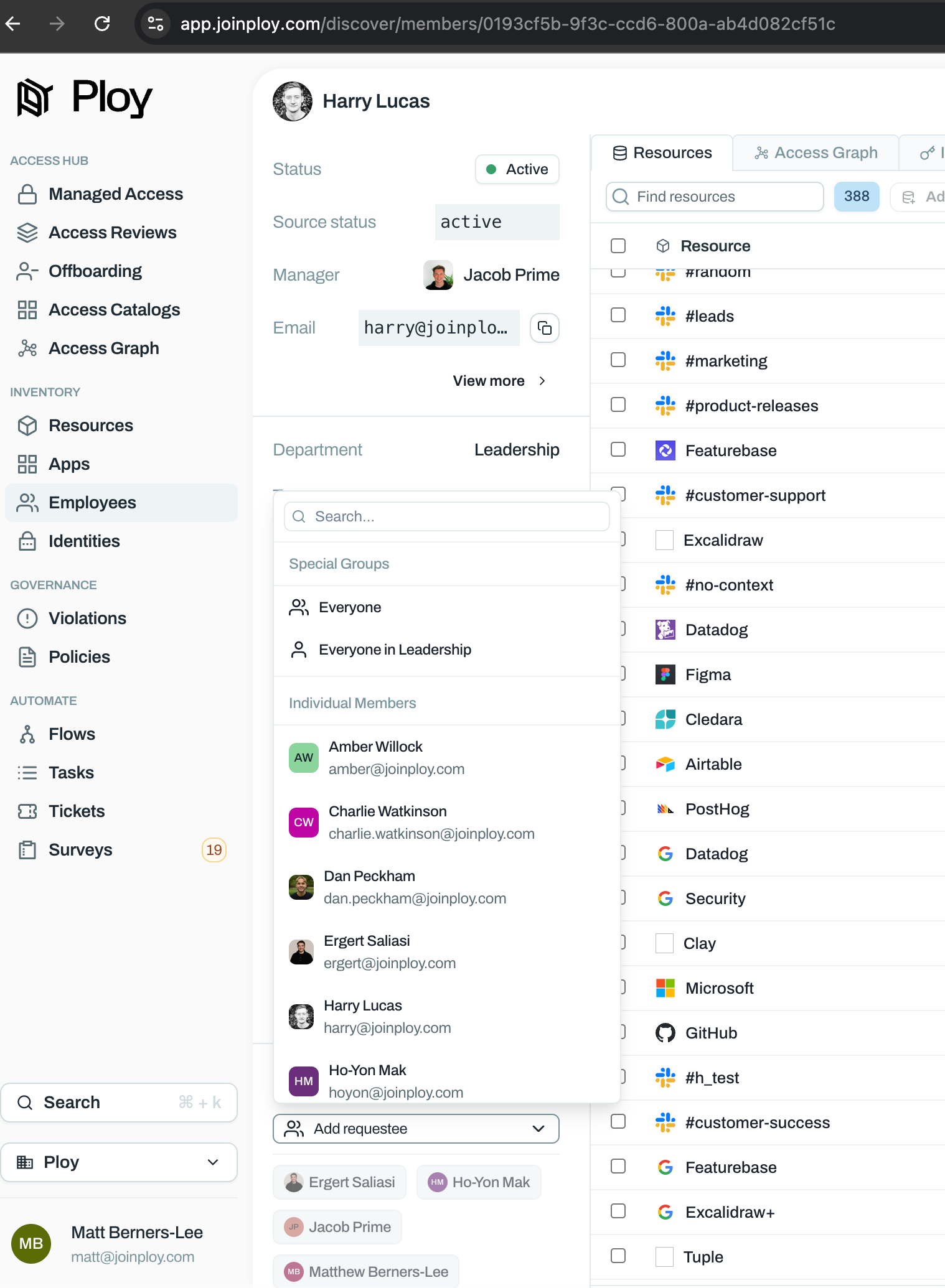
For a while we’ve had the ability to say -
this user can request access on behalf of these other users
Which is done by explicitly specifying each individual for which this can be done. This is useful, for example, when a manager wants to request access to a tool for themselves and a few people in their team.
Now, for extra convenience, it can be done for everyone in the organisation, or by everyone in the same department in the organisation